
KLogWatch
Source (link to git-repo or to original if based on someone elses unmodified work):
Version 2.0.3:
Do proper column sorting on addresses and ports.
Version 2.0.2:
Be sure to save config when a session closes
Add ping command
Actually use dest IP address when doing traceroute on dest IP
Allow use of $(DESTDIR) during installation. Thanks to Tiziano Mueller for the initial patch.
Version 2.0.1:
Fixed error message reporting of an invalid logfile
Version 2.0:
New features:
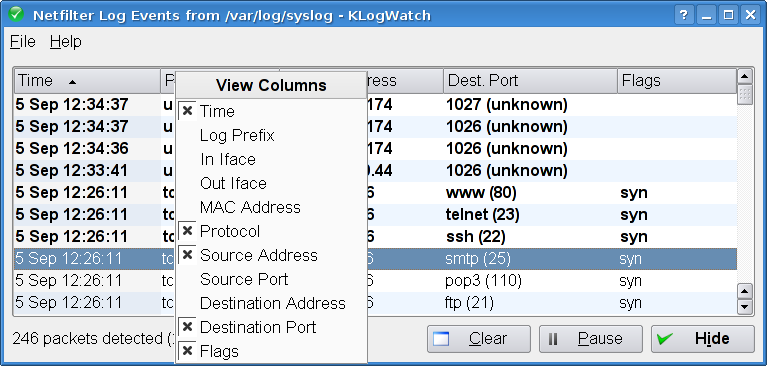
* New columns to account for all netfilter log info
* Select which columns to see
* Column size and order saved
* Window size and position saved
* Right mouse button actions
* Adjustable print font
* Can now print/save window contents or raw log messages
Changes:
* Some code cleanups; more on the way
* Changing configuration does not require restart
* Desktop file installed automatically
* Removed popup on alert action; all alerts appear in the tray
* Debian package files and RPM spec file included
Version 1.8.4:
Fixed bug in Save As option
New cleaner icons
Added uninstall make target
Version 1.8.3:
Corrected to work properly when log-rotation occurs
Use proper KDE config file location
(Copy your ~/.klogwatch to ~/.kde/share/config/klogwatchrc).
Don't scroll down to new packets if window already visible
Version 1.8.2:
Corrected "parsed == false" assertion failure on startup under latest KDE versions.
Version 1.8.1:
Fixed SIGABRT Mandrake problem where /var/log/kernel is a directory
Version 1.8:
Fixed the autoconf system for Fedora/Mandrake/Debian
Added sort by destination port
Lookup protocol numbers in /etc/protocols to give names














Ratings & Comments
32 Comments
just the thing i was looking for. One question though, it says that /var/log/kernel is not found (and i dont have it). I tried dmesg, messages.1, syslog.1, but none when they are loaded nothing is shown... i'm using slackware 12, kernel 2.6.23.12, kde 3.5.7
Never mind the last one, FIXED. i used syslog.1 instead of syslog.
RPM for SLED 10: http://donnie.110mb.com/downloads.php?cat_id=2 For GPG key, please look at the front page of my site.
RPM updated to v2.0.2
We also have an rpm available on the SourceForge site. Nick compiled that one on Suse 10.1, I think. Best, John
Yes, my RPM was built on SUSE 10.1. It's probably very similar to the SLED one though.
Could you tell me the name of those fonts, which are appear on the setup's pictures?
The font in the sample pictures is called "Misc Fixed" (12pt). I don't know where it came from, but I'm using SuSE 10.1 and I believe it came with the distro. Fixed fonts are nicer for klogwatch because thnigs like IP addresses line up. HTH, -nick
It would be nice to have remote support included, so I could watch the logfiles on my servers.
Yes, I can see how that would be useful. But I'd need to build some sort of remote protocol into klogwatch - really that should be done "outside". I've not tried, but it should work via an NFS mount. The program itself only knows about a "file" that contains the logs.
I thought about doing this using NFS, too. But that's too unsecure for some environments. Maybe you find a solution using the KDE kio SSH (fish) implementation. Regards, Elias P.
I'll look into this. Presumably it should be possible to set up some sort of ssh tunnel - I just don't know enough about it to say. Thanks for the suggestion anyway.
Going through the fish kioslave was my first thought too, but I don't know off the top of my head how well it would work to stat and tail a remote file like that. How do you currently do remote logging? There's info out there about how to set up syslog or syslog-ng to securely receive remote log events. I haven't tried it, but I suspect that klogwatch would be able to pick up those alerts in that kind of setup.
Apologies if this is off topic, but is there any chance this app could support snort's analysis of potential attacks, or in some other fashion alert the user if a potential attack is detected? I'm thinking klogwatch would be the perfect tool to combine with guarddog and whatever other security tools are appropriate and create a clone of the Zonealarm experience. Is this possible?
Technically, this probably would be possible, but it's a very different task to the one KLogWatch is currently doing - at the moment, it is simply displaying intercepted packets. There is no attempt to interpret the packets or look for patterns of activity that might indicate an attack.
Would be great, but this would need merging this project with a firewall configurator (eg: Kmyfirewall) and could not, however, select which packet to allow "on the fly" (since logging is done on dropped packets...)
Hi, I just installed KlogWatch on my Gentoo today. Compile & Install went fine and program works ok when I start it, however, after a while (can't tell exactly how long) it seems to stop monitoring. When first started, rejected packets get shown correctly, but then suddenly there's nothing. After restart events get detected properly again. Any ideas what might cause that? And one suggestion: How about adding possibility to configure which events should trigger popup (or system tray) alarm? I don't really care about those gazillions of windows network messages that tend to be blocked :) Then again I guess I could just not log them but would be a nice addition anyway. Thanks for nice piece of software!
Hi, It shouldn't stop monitoring (of course!). How do you know that it's not monitoring the file - new events not registering? If you run KLogWatch from the command line, and use -d (debug), is there any extra information? You should see a "." printed every time it checks the logfile for new content (the Poll interval). I like the other idea. How to specify what you do/don't want to see though. Just by port/protocol?
I tried running from command line with -d option as you suggested, looks like program is still running and sort of monitoring the logfile, ie. "." gets printed to stdout every second (poll interval set to one second). However, events do not get shown after a certain period. There's no errors or anything printed. Ie. I can ping the host and ping events do get logged in logfile, but there's no feedback of any kind in klogwatch, seems it simply won't recognise the event.
OK, I'll try to reproduce it here. To be honest, I might not notice if it stopped monitoring events - these days, you get so many events blocked that I tend to just ignore them all (turn it off, or pause it for 20 minutes).
If it's possible, can you give me a logfile that spans the period when it was working, and includes some packets at the end that are not recognised? If you just tell me the last packet from the log that was found, I can see if there's anything after that (perhaps from another source) that might throw it. Can you mail it to me home address (the freeuk.com address on my profile here, or in the Help panel of the program). Gzipped would help - modem I'm afraid :-)
I don't suppose you have log-rotation configured? Some systems have cron jobs that archive old logs, delete very old logs, and start fresh ones every so often. I'd not thought about this before, but if that happens - so a particular logfile (inode) is no longer being written to - then of course the program wouldn't notice (and I should try to do something about it, like close and re-open the file by name every so often!)
OK, should all be fixed in 1.8.3. The code didn't take account of log-rotation.
Hi. good work! just a question (i don't know if is a stupid one), I use Linux SmoothWall in my gateway (in a i386 oldi) and I really need to monitor the logs of iptables, but this box don't have any graphics lib. or something like. What can I do to compile this program for this kind of distribution and run it in my X11 linux desktop via ssh??? thankyou.
Hi Xavier, KLogWatch just tails a file, so if you can dynamically pull your Netfilter log files back to the graphical machine, KLogWatch will "watch" them for you. I don't know much about ssh and whether it's possible to spool a file continuously between machines like this. Obviously something like an NFS mount should work. Once you've got the file "coming over", you point KLogWatch at it with the -f option (or use the setup menu to change the monitored file). You may really want to find a static log analyiser - ie. one which looks at the logs on a regular basis (say every day) rather than dynamically watching the log file? There are other log tools which do this. HTH,